CryptoDB
Pyjamask: Block Cipher and Authenticated Encryption with Highly Efficient Masked Implementation
| Authors: |
|
|---|---|
| Download: | |
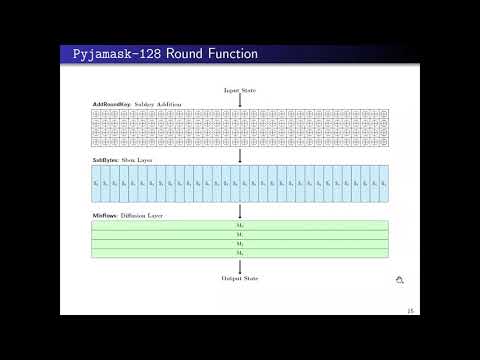
| Abstract: | This paper introduces Pyjamask, a new block cipher family and authenticated encryption proposal submitted to the NIST lightweight cryptography standardization process. Pyjamask targets side-channel resistance as one of its main goal. More precisely, it strongly minimizes the number of nonlinear gates used in its internal primitive in order to allow efficient masked implementations, especially for high-order masking in software. Compared to other block ciphers, our proposal has thus among the smallest number of binary AND computations per input bit at the time of writing. Even though Pyjamask minimizes such an important criterion, it remains rather lightweight and efficient, thanks to a general bitslice construction that enables to computation of all nonlinear gates in parallel. For authenticated encryption, we adopt the provably secure AEAD mode OCB which has been extensively studied and has the benefit to offer full parallelization. Of course, other block cipher-based modes can be considered as well if other performance profiles are to be targeted.The paper first gives the specification of the Pyjamask block cipher and the associated AEAD proposal. We also provide a detailed design rationale for the block cipher which is guided by our aim of software efficiency in the presence of high-order masking. The security of the design is analyzed against most commonly known cryptanalysis techniques. We finally describe efficient (masked) implementations in software and provide implementation results with aggressive performances for masking of very high orders (up to 128). We also provide a rough estimation of the hardware performances which remain much better than those of an AES round-based implementation. |
Video from TOSC 2020
BibTeX
@article{tosc-2020-30510,
title={Pyjamask: Block Cipher and Authenticated Encryption with Highly Efficient Masked Implementation},
journal={IACR Transactions on Symmetric Cryptology},
publisher={Ruhr-Universität Bochum},
volume={2020, Special Issue 1},
pages={31-59},
url={https://tosc.iacr.org/index.php/ToSC/article/view/8617},
doi={10.13154/tosc.v2020.iS1.31-59},
author={Dahmun Goudarzi and Jérémy Jean and Stefan Kölbl and Thomas Peyrin and Matthieu Rivain and Yu Sasaki and Siang Meng Sim},
year=2020
}