CRYPTO 2018: 
Hovav Shacham and Alexandra Boldyreva (Eds.):
Crypto 2018,
Santa Barbara, USA
August 19-23, 2018
Proceedings.
Crypto database info for Crypto 2018
Hovav Shacham and Alexandra Boldyreva (Eds.)
Organizational Committee
Program Committee
Shweta Agrawal
Benny Applebaum
Foteini Baldimtsi
Gilles Barthe
Fabrice Benhamouda
Alex Biryukov
Jeremiah Blocki
Anne Broadbent
Chris Brzuska
Chitchanok Chuengsatiansup
Dana Dachman-Soled
Léo Ducas
Pooya Farshim
Dario Fiore
Marc Fischlin
Georg Fuchsbauer
Steven Galbraith
Christina Garman
Daniel Genkin
Dov Gordon
Viet Tung Hoang
Tetsu Iwata
Stanislaw Jarecki
Seny Kamara
Markulf Kohlweiss
Farinaz Koushanfar
Xuejia Lai
Tancrède Lepoint
Anna Lysyanskaya
Alex J. Malozemoff
Sarah Meiklejohn
Daniele Micciancio
María Naya-Plasencia
Kenny Paterson
Ananth Raghunathan
Mike Rosulek
Ron Rothblum
Alessandra Scafuro
abhi shelat
Nigel Smart
Martijn Stam
Noah Stephens-Davidowitz
Aishwarya Thiruvengadam
Hoeteck Wee
Daniel Wichs
Mark Zhandry
Organizational Committee
Program Chairs:
General Chair:
General Chair:
Hovav Shacham and Alexandra Boldyreva
Tal Rabin
Tal Rabin
Program Committee
Shweta Agrawal
Benny Applebaum
Foteini Baldimtsi
Gilles Barthe
Fabrice Benhamouda
Alex Biryukov
Jeremiah Blocki
Anne Broadbent
Chris Brzuska
Chitchanok Chuengsatiansup
Dana Dachman-Soled
Léo Ducas
Pooya Farshim
Dario Fiore
Marc Fischlin
Georg Fuchsbauer
Steven Galbraith
Christina Garman
Daniel Genkin
Dov Gordon
Viet Tung Hoang
Tetsu Iwata
Stanislaw Jarecki
Seny Kamara
Markulf Kohlweiss
Farinaz Koushanfar
Xuejia Lai
Tancrède Lepoint
Anna Lysyanskaya
Alex J. Malozemoff
Sarah Meiklejohn
Daniele Micciancio
María Naya-Plasencia
Kenny Paterson
Ananth Raghunathan
Mike Rosulek
Ron Rothblum
Alessandra Scafuro
abhi shelat
Nigel Smart
Martijn Stam
Noah Stephens-Davidowitz
Aishwarya Thiruvengadam
Hoeteck Wee
Daniel Wichs
Mark Zhandry
- Secure Messaging
- Towards Bidirectional Ratcheted Key Exchange, 3-32, Bertram Poettering, Paul Rösler
bib info, video - Optimal Channel Security Against Fine-Grained State Compromise: The Safety of Messaging, 33-62, Igors Stepanovs, Joseph Jaeger
bib info, video - Out-of-Band Authentication in Group Messaging: Computational, Statistical, Optimal, 63-89, Gil Segev, Lior Rotem
bib info, video
- Towards Bidirectional Ratcheted Key Exchange, 3-32, Bertram Poettering, Paul Rösler
- Round Optimal MPC
- Round-Optimal Secure Multiparty Computation with Honest Majority, 395-424, Abhishek Jain, Prabhanjan Ananth, Arka Rai Choudhuri, Aarushi Goel
bib info, video - On the Exact Round Complexity of Secure Three-Party Computation, 425-458, Arpita Patra, Divya Ravi
bib info, video - Promise Zero Knowledge and Its Applications to Round Optimal MPC, 459-487, Vipul Goyal, Amit Sahai, Yael Tauman Kalai, Abhishek Jain, Dakshita Khurana, Saikrishna Badrinarayanan
bib info, video - Round-Optimal Secure Multi-Party Computation, 488-520, Shai Halevi, Carmit Hazay, Muthuramakrishnan Venkitasubramaniam, Antigoni Polychroniadou
bib info, video
- Round-Optimal Secure Multiparty Computation with Honest Majority, 395-424, Abhishek Jain, Prabhanjan Ananth, Arka Rai Choudhuri, Aarushi Goel
- Implementations and Physical Attacks
- Foundations
- IACR Distinguished Lecture
From Idea to Impact, the Crypto story: What's next? by Shafi Goldwasser, video - Authenticated and Format-Preserving Encryption
- Fast Message Franking: From Invisible Salamanders to Encryptment, 155-186, Thomas Ristenpart, Yevgeniy Dodis, Joanne Woodage, Paul Grubbs
bib info, video - Indifferentiable Authenticated Encryption, 187-220, Pooya Farshim, Manuel Barbosa
bib info, video - The Curse of Small Domains: New Attacks on Format-Preserving Encryption, 221-251, Stefano Tessaro, Viet Tung Hoang, Ni Trieu
bib info, video
- Fast Message Franking: From Invisible Salamanders to Encryptment, 155-186, Thomas Ristenpart, Yevgeniy Dodis, Joanne Woodage, Paul Grubbs
- Lattices
- GGH15 Beyond Permutation Branching Programs: Proofs, Attacks, and Candidates, 577-607, Vinod Vaikuntanathan, Hoeteck Wee, Yilei Chen
bib info, video - Lower Bounds on Lattice Enumeration with Extreme Pruning, 608-637, Phong Q. Nguyen, Junji Shikata, Yoshinori Aono, Takenobu Seito
bib info, video - Dissection-BKW, 638-666, Alexander May, Felix Heuer, Andre Esser, Robert Kübler, Christian Sohler
bib info, video
- GGH15 Beyond Permutation Branching Programs: Proofs, Attacks, and Candidates, 577-607, Vinod Vaikuntanathan, Hoeteck Wee, Yilei Chen
- Cryptanalysis
- Cryptanalysis via Algebraic Spans, 255-274, Boaz Tsaban, Adi Ben-Zvi, Arkadius Kalka
bib info , video - Improved Division Property Based Cube Attacks Exploiting Algebraic Properties of Superpoly, 275-305, Willi Meier, Takanori Isobe, Qingju Wang, Yosuke Todo, Yonglin Hao, Chaoyun Li
bib info, video - Generic Attacks Against Beyond-Birthday-Bound MACs, 306-336, Mridul Nandi, Gaëtan Leurent, Ferdinand Sibleyras
bib info, video
- Cryptanalysis via Algebraic Spans, 255-274, Boaz Tsaban, Adi Ben-Zvi, Arkadius Kalka
- Lattice-based Zero Knowledge
- Sub-linear Lattice-Based Zero-Knowledge Arguments for Arithmetic Circuits, 669-699, Jens Groth, Vadim Lyubashevsky, Carsten Baum, Jonathan Bootle, Andrea Cerulli, Rafael del Pino
bib info, video - Lattice-Based Zero-Knowledge Arguments for Integer Relations, 700-732, Benoît Libert, Huaxiong Wang, San Ling, Khoa Nguyen
bib info, video - Multi-Theorem Preprocessing NIZKs from Lattices, 733-765, David J. Wu, Sam Kim
bib info
- Sub-linear Lattice-Based Zero-Knowledge Arguments for Arithmetic Circuits, 669-699, Jens Groth, Vadim Lyubashevsky, Carsten Baum, Jonathan Bootle, Andrea Cerulli, Rafael del Pino
- Searchable Encryption and Differential Privacy
- Structured Encryption and Leakage Suppression, 339-370, Seny Kamara, Tarik Moataz, Olya Ohrimenko
bib info - Searchable Encryption with Optimal Locality: Achieving Sublogarithmic Read Efficiency, 371-406, Charalampos Papamanthou, Dimitrios Papadopoulos, Ioannis Demertzis
bib info, video - Tight Tradeoffs in Searchable Symmetric Encryption, 407-436, Gil Segev, Gilad Asharov, Ido Shahaf
bib info, video - Hardness of Non-interactive Differential Privacy from One-Way Functions, 437-466, Tal Malkin, Daniel Wichs, Jonathan Ullman, Lucas Kowalczyk
bib info, video - Risky Traitor Tracing and New Differential Privacy Negative Results, 467-497, Brent Waters, Venkata Koppula, Rishab Goyal, Andrew Russell
bib info
- Structured Encryption and Leakage Suppression, 339-370, Seny Kamara, Tarik Moataz, Olya Ohrimenko
- Efficient MPC
- SPD
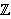 2^k: Efficient MPC mod 2k for Dishonest Majority, 769-798, Ronald Cramer, Chaoping Xing, Peter Scholl, Ivan Damgård, Daniel Escudero
2^k: Efficient MPC mod 2k for Dishonest Majority, 769-798, Ronald Cramer, Chaoping Xing, Peter Scholl, Ivan Damgård, Daniel Escudero
bib info, video - Yet Another Compiler for Active Security or: Efficient MPC Over Arbitrary Rings, 799-829, Claudio Orlandi, Mark Simkin, Ivan Damgård
bib info, video - TinyKeys: A New Approach to Efficient Multi-Party Computation, 3-33, Carmit Hazay, Emmanuela Orsini, Peter Scholl, Eduardo Soria-Vazquez
bib info, video - Fast Large-Scale Honest-Majority MPC for Malicious Adversaries, 34-64, Yehuda Lindell, Daniel Genkin, Koki Hamada, Dai Ikarashi, Koji Chida, Ryo Kikuchi, Ariel Nof
bib info, video
- SPD
- Secret Sharing
- Quantum Cryptography I
- Encryption
- Threshold Cryptosystems from Threshold Fully Homomorphic Encryption, 565-596, Dan Boneh, Rosario Gennaro, Amit Sahai, Steven Goldfeder, Aayush Jain, Sam Kim, Peter M. R. Rasmussen
bib info, video - Multi-Input Functional Encryption for Inner Products: Function-Hiding Realizations and Constructions Without Pairings, 597-627, Michel Abdalla, Dario Catalano, Dario Fiore, Romain Gay, Bogdan Ursu
bib info, video
- Threshold Cryptosystems from Threshold Fully Homomorphic Encryption, 565-596, Dan Boneh, Rosario Gennaro, Amit Sahai, Steven Goldfeder, Aayush Jain, Sam Kim, Peter M. R. Rasmussen
- Quantum Cryptography II
- Pseudorandom Quantum States, 126-152, Fang Song, Yi-Kai Liu, Zhengfeng Ji
bib info, video - Quantum Attacks Against Indistinguishablility Obfuscators Proved Secure in the Weak Multilinear Map Model, 153-183, Alice Pellet-Mary
bib info - Cryptanalyses of Branching Program Obfuscations over GGH13 Multilinear Map from the NTRU Problem, 184-210, Jung Hee Cheon, Changmin Lee, Minki Hhan, Jiseung Kim
bib info, video
- Pseudorandom Quantum States, 126-152, Fang Song, Yi-Kai Liu, Zhengfeng Ji
- Symmetric Cryptography
- Encrypt or Decrypt? To Make a Single-Key Beyond Birthday Secure Nonce-Based MAC, 631-661, Mridul Nandi, Kan Yasuda, Nilanjan Datta, Avijit Dutta
bib info, video - Rasta: A Cipher with Low ANDdepth and Few ANDs per Bit, 662-692, Christian Rechberger, Gregor Leander, Florian Mendel, Eik List, Maria Eichlseder, Virginie Lallemand, Christoph Dobraunig, Lorenzo Grassi
bib info, video - Non-Uniform Bounds in the Random-Permutation, Ideal-Cipher, and Generic-Group Models, 693-721, Yevgeniy Dodis, Sandro Coretti, Siyao Guo
bib info, video - Provable Security of (Tweakable) Block Ciphers Based on Substitution-Permutation Networks, 722-753, Jonathan Katz, Yevgeniy Dodis, John P. Steinberger, Jooyoung Lee, Aishwarya Thiruvengadam, Benoît Cogliati, Zhe Zhang
bib info, video
- Encrypt or Decrypt? To Make a Single-Key Beyond Birthday Secure Nonce-Based MAC, 631-661, Mridul Nandi, Kan Yasuda, Nilanjan Datta, Avijit Dutta
- MPC
- An Optimal Distributed Discrete Log Protocol with Applications to Homomorphic Secret Sharing, 213-242, Nathan Keller, Itai Dinur, Ohad Klein
bib info, video - Must the Communication Graph of MPC Protocols be an Expander?, 243-272, Elette Boyle, Pavel Hubáĉ, Deepesh Data, Ran Cohen
bib info, video - Two-Round Multiparty Secure Computation Minimizing Public Key Operations, 273-301, Sanjam Garg, Akshayaram Srinivasan, Peihan Miao
bib info, video - Limits of Practical Sublinear Secure Computation, 302-332, Yuval Ishai, Elette Boyle, Antigoni Polychroniadou
bib info, video
- An Optimal Distributed Discrete Log Protocol with Applications to Homomorphic Secret Sharing, 213-242, Nathan Keller, Itai Dinur, Ohad Klein
- Proofs of Work and Proofs of Stake
- Verifiable Delay Functions (paper not available), 757-788, Dan Boneh, Joseph Bonneau, Ben Fisch, Benedikt Bünz
bib info, video- Proofs of Work From Worst-Case Assumptions, 789-819, Alon Rosen, Prashant Nalini Vasudevan, Marshall Ball, Manuel Sabin
bib info, video - Proofs of Work From Worst-Case Assumptions, 789-819, Alon Rosen, Prashant Nalini Vasudevan, Marshall Ball, Manuel Sabin
- Verifiable Delay Functions (paper not available), 757-788, Dan Boneh, Joseph Bonneau, Ben Fisch, Benedikt Bünz
- Garbling
- Limits on the Power of Garbling Techniques for Public-Key Encryption, 335-364, Sanjam Garg, Mohammad Mahmoody, Mohammad Hajiabadi, Ameer Mohammed
bib info, video - Optimizing Authenticated Garbling for Faster Secure Two-Party Computation, 365-391, Jonathan Katz, Mike Rosulek, Samuel Ranellucci, Xiao Wang
bib info, video
- Limits on the Power of Garbling Techniques for Public-Key Encryption, 335-364, Sanjam Garg, Mohammad Mahmoody, Mohammad Hajiabadi, Ameer Mohammed
- Invited Talk
Crypto: a Key Ingredient to Building Respectful Products, by Lea Kissner, video - Proof Tools
- Simplifying Game-Based Definitions, 3-32, Phillip Rogaway, Yusi Zhang
bib info, video - The Algebraic Group Model and its Applications, 33-62, Eike Kiltz, Georg Fuchsbauer, Julian Loss
bib info, video - Information-Theoretic MPC
- Amortized Complexity of Information-Theoretically Secure MPC Revisited, 395-426, Ronald Cramer, Chaoping Xing, Ignacio Cascudo, Chen Yuan
bib info, video - Private Circuits: A Modular Approach, 427-455, Amit Sahai, Yuval Ishai, Prabhanjan Ananth
bib info, video
- Simplifying Game-Based Definitions, 3-32, Phillip Rogaway, Yusi Zhang
- Key Exchange
- Various Topics
- Symmetric Cryptanalysis
- Improved Key Recovery Attacks on Reduced-Round AES with Practical Data and Memory Complexities, 185-212, Orr Dunkelman, Nathan Keller, Adi Shamir, Achiya Bar-On, Eyal Ronen
bib info - Fast Correlation Attack Revisited, 129-159, Kazumaro Aoki, Willi Meier, Bin Zhang, Takanori Isobe, Yosuke Todo
bib info, video - A Key-Recovery Attack on 855-round Trivium, 160-184, Willi Meier, Xiaoyun Wang, Xiaoyang Dong, Ximing Fu
bib info, video - Bernstein Bound on WCS is Tight, 213-238, Mridul Nandi
bib info, video
- Improved Key Recovery Attacks on Reduced-Round AES with Practical Data and Memory Complexities, 185-212, Orr Dunkelman, Nathan Keller, Adi Shamir, Achiya Bar-On, Eyal Ronen
- Oblivious Transfer and Non-Malleable Codes
- Adaptive Garbled RAM from Laconic Oblivious Transfer, 515-544, Rafail Ostrovsky, Sanjam Garg, Akshayaram Srinivasan
bib info - On the Round Complexity of OT Extension, 545-574, Sanjam Garg, Mohammad Mahmoody, Daniel Masny, Izaak Meckler
bib info, video - Non-Malleable Codes for Partial Functions with Manipulation Detection, 577-607, Aggelos Kiayias, Feng-Hao Liu, Yiannis Tselekounis
bib info, video - Continuously Non-Malleable Codes in the Split-State Model from Minimal Assumptions, 608-639, Giuseppe Persiano, Ivan Visconti, Rafail Ostrovsky, Daniele Venturi
bib info, video
- Adaptive Garbled RAM from Laconic Oblivious Transfer, 515-544, Rafail Ostrovsky, Sanjam Garg, Akshayaram Srinivasan
- Hashes and Random Oracles
- Correcting Subverted Random Oracles, 241-271, Moti Yung, Alexander Russell, Qiang Tang, Hong-Sheng Zhou
bib info, video - Combiners for Backdoored Random Oracles, 272-302, Pooya Farshim, Sogol Mazaheri, Balthazar Bauer
bib info, video - On Distributional Collision Resistant Hashing, 303-327, Ilan Komargodski, Eylon Yogev
bib info, video
- Correcting Subverted Random Oracles, 241-271, Moti Yung, Alexander Russell, Qiang Tang, Hong-Sheng Zhou
- Zero Knowledge
- Non-Interactive Zero-Knowledge Proofs for Composite Statements, 643-673, Payman Mohassel, Shashank Agrawal, Chaya Ganesh
bib info, video - From Laconic Zero-Knowledge to Public-Key Cryptography, 674-697, Itay Berman, Ron D. Rothblum, Prashant Nalini Vasudevan, Akshay Degwekar
bib info, video - Updatable and Universal Common Reference Strings with Applications to zk-SNARKs, 698-728, Jens Groth, Markulf Kohlweiss, Sarah Meiklejohn, Ian Miers, Mary Maller
bib info, video
- Non-Interactive Zero-Knowledge Proofs for Composite Statements, 643-673, Payman Mohassel, Shashank Agrawal, Chaya Ganesh
- Trapdoor Functions
- Obfuscation
- On the Complexity of Compressing Obfuscation, 753-783, Rafael Pass, Gilad Asharov, Ilan Komargodski, Naomi Ephraim
bib info, video - A Simple Obfuscation Scheme for Pattern-Matching with Wildcards, 731-752, Tal Malkin, Mariana Raykova, Valerio Pastro, Allison Bishop, Lucas Kowalczyk, Kevin Shi
bib info, video
- On the Complexity of Compressing Obfuscation, 753-783, Rafael Pass, Gilad Asharov, Ilan Komargodski, Naomi Ephraim