CryptoDB
Key Assignment Schemes with Authenticated Encryption, revisited
| Authors: |
|
|---|---|
| Download: | |
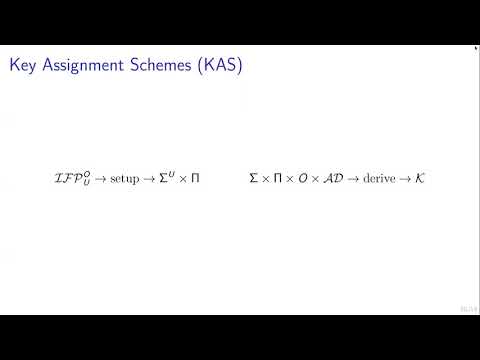
| Abstract: | A popular cryptographic option to implement Hierarchical Access Control in organizations is to combine a key assignment scheme with a symmetric encryption scheme. In brief, key assignment associates with each object in the hierarchy a unique symmetric key, and provides all higher-ranked “authorized” subjects with a method to recover it. This setup allows for encrypting the payloads associated with the objects so that they can be accessed by the authorized and remain inaccessible for the unauthorized. Both key assignment and symmetric encryption have been researched for roughly four decades now, and a plethora of efficient constructions have been the result. Surprisingly, a treatment of the joint primitive (key assignment combined with encryption, as used in practice) in the framework of provable security was conducted only very recently, leading to a publication in ToSC 2018(4). We first carefully revisit this publication. We then argue that there are actually two standard use cases for the combined primitive, which also require individual treatment. We correspondingly propose a fresh set of security models and provably secure constructions for each of them. Perhaps surprisingly, the two constructions call for different symmetric encryption primitives: While standard AEAD is the right tool for the one, we identify a less common tool called Encryptment as best fitting the other. |
Video from TOSC 2020
BibTeX
@article{tosc-2020-30537,
title={Key Assignment Schemes with Authenticated Encryption, revisited},
journal={IACR Transactions on Symmetric Cryptology},
publisher={Ruhr-Universität Bochum},
volume={2020, Issue 2},
pages={40-67},
url={https://tosc.iacr.org/index.php/ToSC/article/view/8668},
doi={10.13154/tosc.v2020.i2.40-67},
author={Jeroen Pijnenburg and Bertram Poettering},
year=2020
}