CryptoDB
Breaking CAS-Lock and Its Variants by Exploiting Structural Traces
| Authors: |
|
|---|---|
| Download: | |
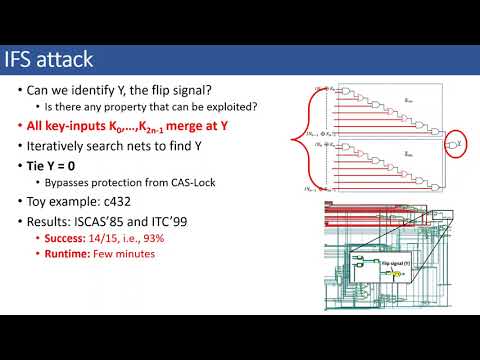
| Abstract: | Logic locking is a prominent solution to protect against design intellectual property theft. However, there has been a decade-long cat-and-mouse game between defenses and attacks. A turning point in logic locking was the development of miterbased Boolean satisfiability (SAT) attack that steered the research in the direction of developing SAT-resilient schemes. These schemes, however achieved SAT resilience at the cost of low output corruption. Recently, cascaded locking (CAS-Lock) [SXTF20a] was proposed that provides non-trivial output corruption all-the-while maintaining resilience to the SAT attack. Regardless of the theoretical properties, we revisit some of the assumptions made about its implementation, especially about security-unaware synthesis tools, and subsequently expose a set of structural vulnerabilities that can be exploited to break these schemes. We propose our attacks on baseline CAS-Lock as well as mirrored CAS (M-CAS), an improved version of CAS-Lock. We furnish extensive simulation results of our attacks on ISCAS’85 and ITC’99 benchmarks, where we show that CAS-Lock/M-CAS can be broken with ∼94% success rate. Further, we open-source all implementation scripts, locked circuits, and attack scripts for the community. Finally, we discuss the pitfalls of point function-based locking techniques including Anti-SAT [XS18] and Stripped Functionality Logic Locking(SFLL-HD) [YSN+17], which suffer from similar implementation issues. |
Video from TCHES 2021
BibTeX
@article{tches-2021-31290,
title={Breaking CAS-Lock and Its Variants by Exploiting Structural Traces},
journal={IACR Transactions on Cryptographic Hardware and Embedded Systems},
publisher={Ruhr-Universität Bochum},
volume={2021, Issue 3},
pages={418-440},
url={https://tches.iacr.org/index.php/TCHES/article/view/8981},
doi={10.46586/tches.v2021.i3.418-440},
author={Abhrajit Sengupta and Nimisha Limaye and Ozgur Sinanoglu},
year=2021
}