CryptoDB
Anonymous Public Key Encryption under Corruptions
| Authors: |
|
|---|---|
| Download: | |
| Presentation: | Slides |
| Conference: | ASIACRYPT 2022 |
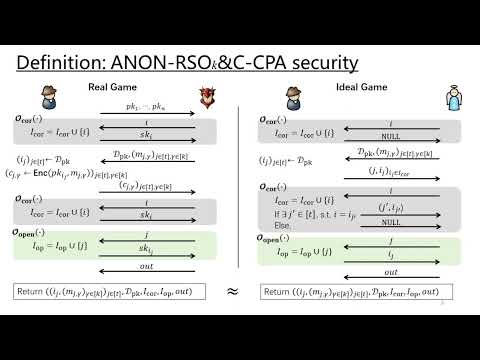
| Abstract: | Anonymity of public key encryption (PKE) requires that, in a multi-user scenario, the PKE ciphertexts do not leak information about which public keys are used to generate them. Corruptions are common threats in the multi-user scenario but anonymity of PKE under corruptions is less studied in the literature. In TCC 2020, Benhamouda et al. first provide a formal characterization for anonymity of PKE under a specific type of corruption. However, no known PKE scheme is proved to meet their characterization. To the best of our knowledge, all the PKE application scenarios which require anonymity also require confidentiality. However, in the work by Benhamouda et al., different types of corruptions for anonymity and confidentiality are considered, which can cause security pitfalls. What's worse, we are not aware of any PKE scheme which can provide both anonymity and confidentiality under the same types of corruptions. In this work, we introduce a new security notion for PKE called ANON-RSO$_{k}\&$C security, capturing anonymity under corruptions. We also introduce SIM-RSO$_{k}\&$C security which captures confidentiality under the same types of corruptions. We provide a generic framework of constructing PKE scheme which can achieve the above two security goals simultaneously based on a new primitive called key and message non-committing encryption (KM-NCE). Then we give a general construction of KM-NCE utilizing a variant of hash proof system (HPS) called Key-Openable HPS. We also provide Key-Openable HPS instantiations based on the matrix decisional Diffie-Hellman assumption. Therefore, we can obtain various concrete PKE instantiations achieving the two security goals in the standard model with \emph{compact} ciphertexts. Furthermore, for some PKE instantiation, its security reduction is \emph{tight}. |
Video from ASIACRYPT 2022
BibTeX
@inproceedings{asiacrypt-2022-32529,
title={Anonymous Public Key Encryption under Corruptions},
publisher={Springer-Verlag},
author={Zhengan Huang and Junzuo Lai and Shuai Han and Lin Lyu and Jian Weng},
year=2022
}